If you receive a text like this one, it appears to be (and is) a legitimate one from Meta. However, you are very likely being hacked!

I get contacted on a regular basis about hacked accounts and how to recover them. This particular case had me stumped for a while; ingenious hackers were able to re-gain access to an account after it was reset by Meta, after they even had completed facial verification and ID checks… with multi-factor authentication switched on!
The Short Version (TL;DR)
- Ensure you have multi-factor authentication (MFA) on all accounts, where available. Where MFA is unavailable, use a strong password and a password manager
- NEVER click on a link or send a screenshot of a message to “a friend”
- If you have been hacked and are able to recover your account, reset your backup codes immediately and turn on multi-factor afterwards (do not assume that just because you have recovered your account, that the hackers no longer have access!) – details below
- Use an authenticator app (vs SMS) for multi-factor authentication
The Full Version – What Actually Happened?
I was contacted by a friend who tried to get their Instagram account back.
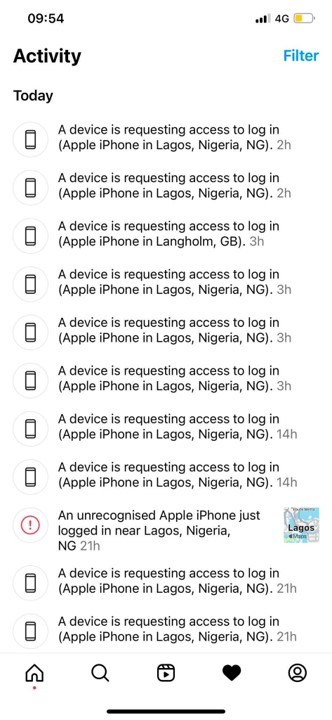
He had accidentally shared information with one of his supposed friends (also a hacked account) that allowed the hackers to take control of his own account.
After he eventually recovered his account, I was amazed and honestly quite impressed that the hackers managed to re-gain access, even though he had multi-factor authentication turned on. At first I thought they might have access to his email account, but they didn’t.
I like to try and work out how sophisticated hackers really are; engage in some conversation and work out how they did it.
I pretended I didn’t know my friend had been hacked (again!) to see how long it might take for them to target me:
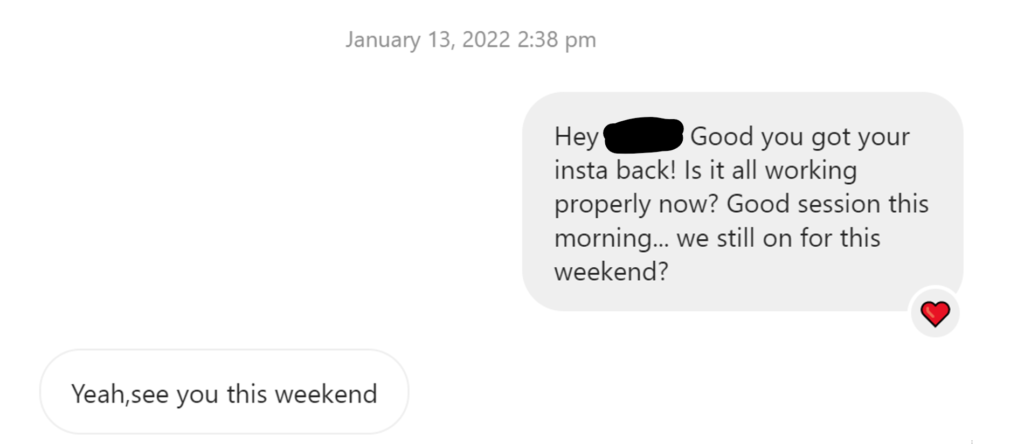
Sure enough, later that day…
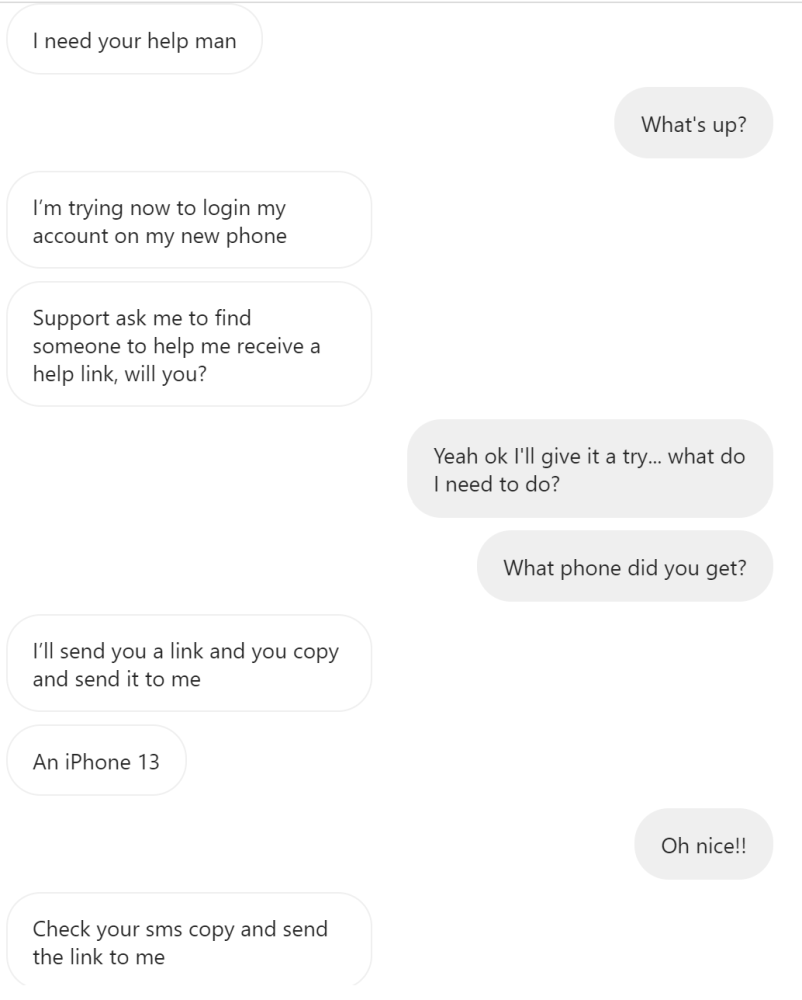
Obviously I didn’t click on a password reset link or copy anything and send it back to them.
If I had done so, they’d have likely taken control of my account too if I wasn’t careful.
It transpires when they gained access to my friend’s account, they copied the MFA backup codes, and used them to get back in.
After Meta had completed ID checks including facial verification (this in itself was problematic – ensure you send them a video wearing similar clothing to some of your posts, with similar background if possible… may sound silly but it was necessary!) – they didn’t reset the backup recovery codes for MFA! Which was madness, as it left his account wide open!
Recovery codes are in the Instagram app under Security > Two-factor authentication > Additional methods
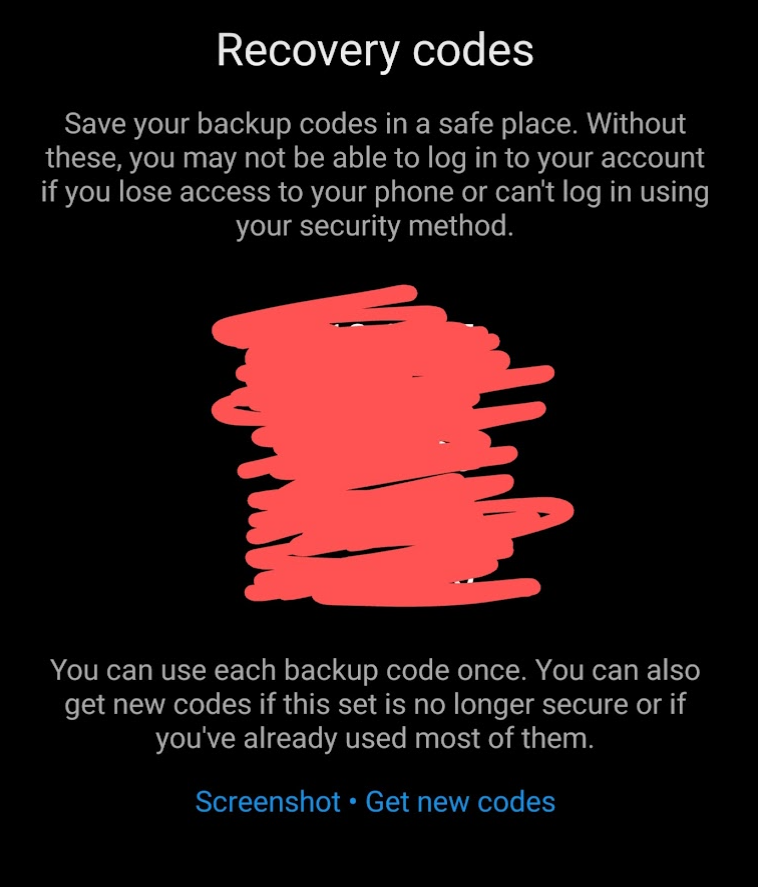
If you have the Backup codes, you can get back into an account even after the password has been changed… even with two-factor authentication on!
I raised this as an issue with Meta but they claimed that it’s not a security flaw, it’s “by design” – which to me seems ridiculous, that they would confirm 100% that an account is owned by a user who’s been hacked (ID & facial verification etc.) but leave the backdoor open…
Whatever you do, keep your backup / recovery codes in a very safe and protected place. All (if not all) services that have a multi-factor authentication option should provide these codes.
Use an authenticator app instead of SMS where it is available, and turn off SMS as a multi-factor authentication method. It’s a tiny bit more work (debatable) for a lot more security!
When we launched BLOKK it seemed like an obvious feature for us to build, to protect users from social engineering attempts such as this one, by blocking typical password reset URLs and flagging to the user they maybe under attack.
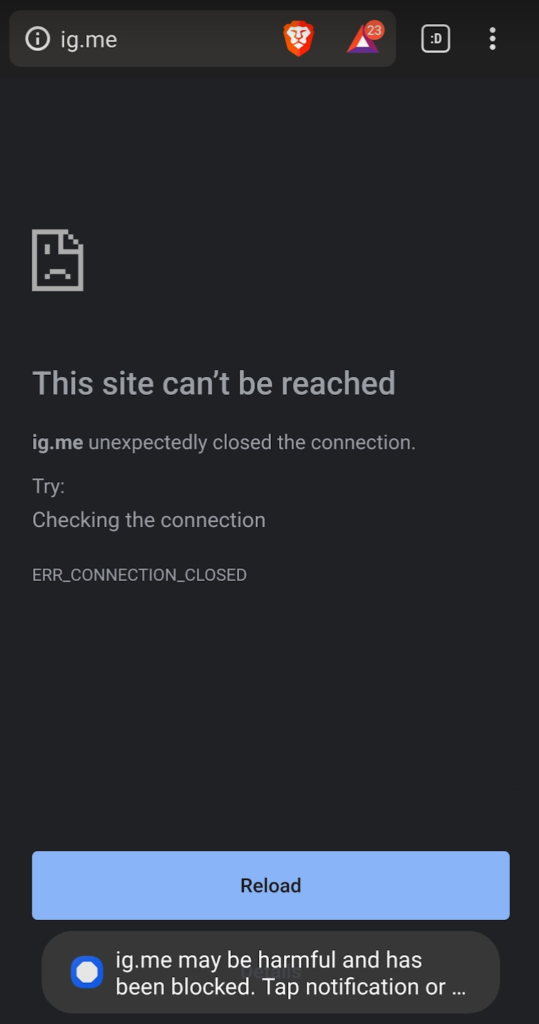
The password reset URL is blocked by default. The user may have been trying to reset their own password, but most likely to be a victim of social engineering. This should highlight to them that there may be a problem.
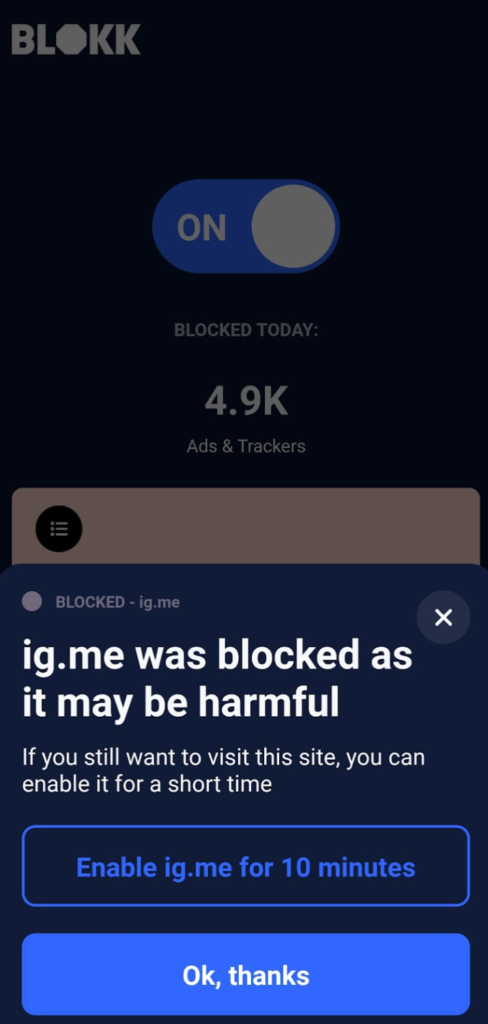
We will be improving the messaging to reference specific risks of social engineering; however, the protection is there already and will prevent others from falling into the same trap.
Whether you use BLOKK or not, I hope this story helps to highlight an issue that I’ve since seen many times and helps to prevent it from happening again.
Feedback welcome in the comments!

Leave a Reply