In our line of work, we see how the true cloud offers unrivalled power, security and flexibility to businesses – but we also see how the cloud is probably one of the most over-hyped and misrepresented technology innovations we are ever likely to encounter. This has even led to the term “cloud washing” due to the popularity of the term “cloud” and its frequent inappropriate use leading to a lot of confusion.
Following on from Mark Loane’s post “Secure your future in the cloud” in 2015, it’s clear that confusion still remains, particularly in the primary jurisdictions that we operate in – Jersey and Guernsey.
This blog aims to highlight and debunk the myths that we encounter the most – and everything is backed up by credible, third party sources, so you don’t just have to take my word for it!
Myth 1: Your data is less secure in the cloud
This is an easy myth to dispel; the sheer amount of financial, technological and human resources that the large public cloud providers have at their disposal means that their data security far surpasses the vast majority of on-premises options.
For example, Microsoft hires teams of ‘hackers’ to constantly ‘attack’ their cloud for vulnerabilities, a process they call red teaming. This ensures their cloud security is constantly being tested and updated by the best in the world. They describe this process as “the data protection equivalent of hiring a UFC fighter to attack you at random, unexpected times… It’s saying: Let’s assume the worst and act accordingly. Because even if you never get invaded, it’s nice to know the army is training for every possible scenario.”
Google employs more than 500 full-time security and privacy professionals and Amazon offers significant data encryption capabilities, strategies for prevention of Distributed Denial of Service attacks (DDoS), a Key Management Service and a multitude of other security features that allow your data to be more secure in the cloud, not less.
All major cloud providers offer a form of Multi-Factor Authentication – for example, using SMS or secondary email to confirm your identity – this best practice is more difficult and far more expensive to implement on-premises.
Even as a provider of hosted services, it is simply not possible to claim that data stored on island is more secure than data stored in the cloud – in fact, in their security seminar held in Jersey last year, KPMG stated that the security in the main vendor clouds is better than many companies can afford to implement by themselves.
Myth 2: You have a legal obligation to keep your data on island
There is no legal reason to keep data on island. There is, however, legislation in the Channel Islands –Data Protection (Jersey) Law 2005 and the Data Protection (Bailiwick of Guernsey) Law, 2001 – which is concerned with the principles of good information handling.
The relevant areas that the legislation covers (summarised in the Data Controllers Overview of Data Protection Law) in relation to the cloud are as follows:
1. Security
Data controllers must take security measures to safeguard personal data.
This is the case regardless of where data is stored, however with the features and capabilities of the major cloud providers, this is usually easier in the cloud than on-premises.
2. Data Location
There is a restriction on the transfer of data outside the EEA (which consists of the EU Member States, Norway, Iceland and Liechtenstein).
As always, understanding where data is stored is important; many of the cloud providers can provide details on the location that data is stored. A risk assessment should be undertaken by a Data Controller including the nature and location of any data, this is no different for data hosted locally or in the cloud.
Myth 3: Public cloud providers lock you in
A valid aspect to investigate in the procurement of any IT vendor’s services where data is concerned is the potential for vendor lock-in. In other words, if you were not happy with the service, or if you want to migrate to another provider for whatever reason, can you – and how difficult would it be?
Historically with IT vendors there was a real risk of provider lock-in – CIOs would be making bets that would involve allegiance to a particular vendor for a number of years.
Whilst this risk is a valid concern with some cloud providers (particularly with Software as a Service) Amazon vice-president Andy Jassy states “We have to earn our customers’ business every hour, every week. If they want to leave they can leave”.
Microsoft takes a similar approach – “It’s your data”. You can download a copy of all of your data at any time and for any reason, without any assistance from Microsoft, and upon expiration or termination of a contract that data is still available for 90 days.
A careful review of local cloud provider terms with regards to lock-in and contracts is strongly recommended – and it’s worth remembering that the major vendor clouds often provide you with far more flexibility in this area.
Myth 4: All clouds are created equal
As already mentioned, the term “cloud washing” was coined in about 2009 to label the sadly common practice by technology service providers of including the term “cloud” with ALL products and services they offer even when, strictly speaking, they weren’t true cloud. This practice resulted in confusion in the marketplace that unfortunately continues today – all clouds are definitely not created equal!
Here’s a brief overview of the common terms used in the industry to describe the types of cloud available in the marketplace:
Public Cloud
The term Public Cloud is typically used to describe the likes of Microsoft, Amazon and Google. The data you store in the public cloud is hosted at the providers’ huge data centres, and while this infrastructure is shared between you and other users, data is isolated between one customer and the next, so nobody but you can access your data.
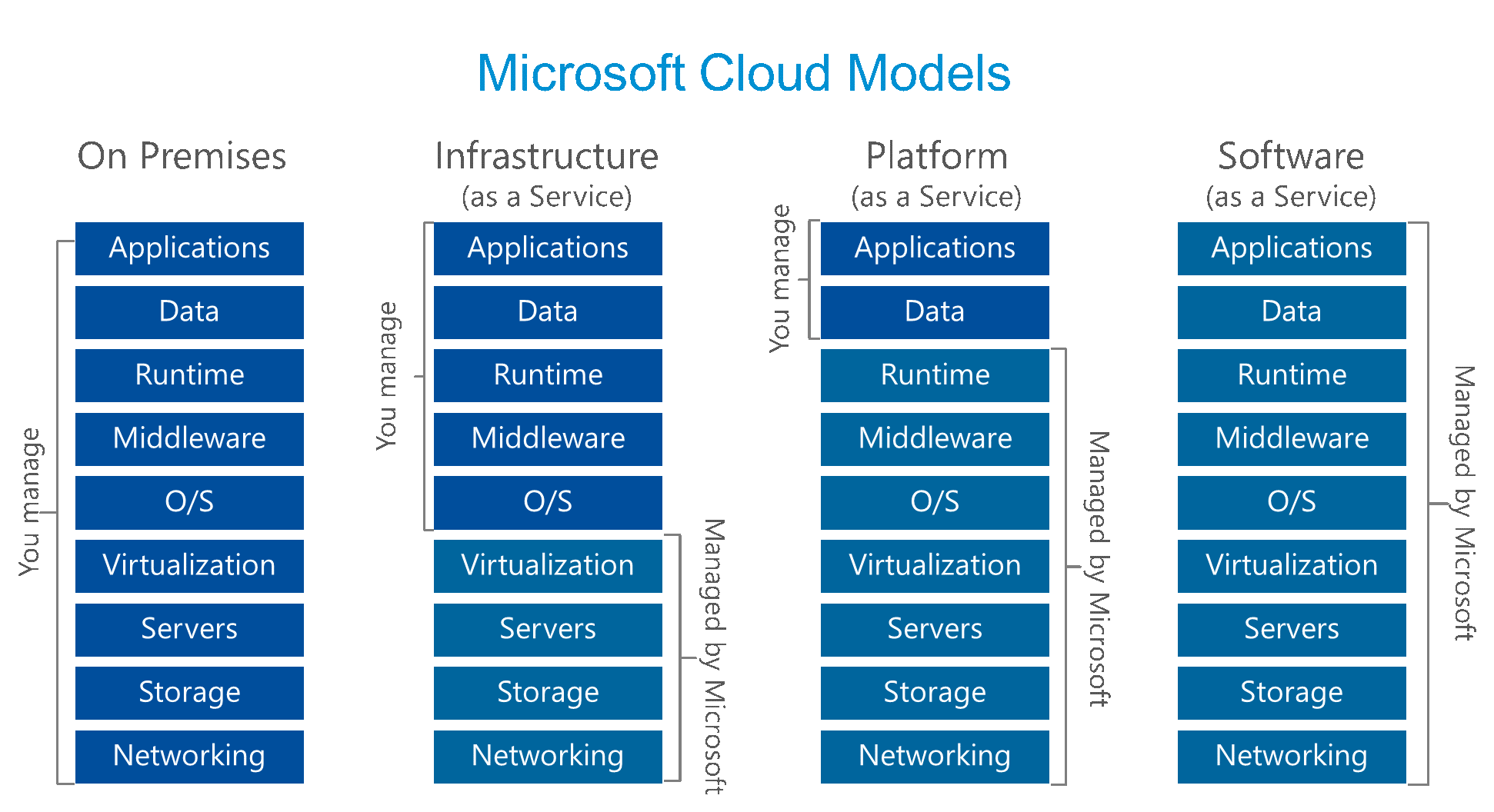
Public clouds are the most cost-effective options for providing the scalability and security features required for enterprise. The larger cloud providers offer Software as a Service in addition to Infrastructure as a Service and Platform as a Service options. Confused? Here’s a quick breakdown of what these terms mean – which the table below also clarifies:
Infrastructure as a Service (IaaS) – this is a service that provides the ‘nuts and bolts’ of computing, including networking, storage, and virtual servers. The main advantage of IaaS is that there is no need to purchase hardware of any kind, it is factored into the service by the provider.
Platform as a Service (PaaS) – this service provides you with a platform where you can develop your own applications leveraging standardised approaches and services; PaaS options do not even require you to install and manage the operating system. For example, SQL Azure is a PaaS version of Microsoft’s SQL Server that is offered as a service to develop applications against; when using SQL Azure there is no access to the underlying operating system, only to the database itself. You manage your data and applications.
Software as a Service (SaaS) – this service is the ‘full package’, providing you with all the tools you need as an end user. Mostly delivered over the internet, Software as a Service encompasses platforms such as Office 365 services (Email, SharePoint Online, Skype for Business etc.), which are provided as a utility type of service.
The following Cloud Model diagram illustrates the general differences between Infrastructure, Platform and Software as a Service from a Microsoft perspective; however the principles apply to all providers:
Private Cloud
A private cloud usually consists of bespoke infrastructure developed and managed for your business either by a local data centre or in-house.
In the above example, private clouds are either On Premises or Infrastructure as a Service.
Technically the “cloud” term could be used for both an On Premises environment or a hosted environment, however there are significant differences between anything hosted on-premises or in a private cloud in a local data centre, and using the public cloud.
The following table lists the differences between hosting on-island in a private cloud, and, for example, in Microsoft’s Azure and/or Office 365 public clouds:
| Area | On-premises or locally hosted | Microsoft Azure or Office 365 |
| Elasticity – ability to scale | Limited to the hardware originally specified and/or capabilities of the virtualisation software | Unlimited |
| Compliance | Difficult and/or expensive to achieve compliance with certain standards. | Compliant with ISO 27001, EU Model Clauses, HIPAA BAA, and FISMA |
| Security | Reliance on security professionals conducting regular checks, penetration tests, patching of servers and firewalls. Expensive to maintain Multi-Factor Authentication. | Dedicated teams maintaining the highest possible levels of security by default. Multi-Factor Authentication available for free or cost-effectively. |
| Cost | A lot more expensive | A lot cheaper |
| Patching | Requires regular maintenance and downtime | Included by default in the majority of cases (all SaaS options and most IaaS options) |
| Data Protection | Risk assessment | Risk assessment |
| Availability | Requires significant investment to achieve 99.9% availability | Financially-backed 99.9%+availability for the majority of services. Uptime reports for Microsoft are available which demonstrate a higher than 99.9% availability for the past 2 years. |
Myth 5: Data in the cloud is easier for law enforcement to access
There is a common misconception that if data is stored with Microsoft, for example, that law enforcement agencies can snoop on the data easily.
Microsoft in particular is extremely transparent about requests for access to data by law enforcement; the numbers are quite surprising, published in the Transparency Hub:
“How many enterprise cloud customers were impacted by law enforcement requests?
In the second half of 2015, Microsoft received fourteen requests from law enforcement for thirty-five accounts associated with enterprise cloud customers. In nine cases, the requests were rejected or law enforcement was successfully redirected to the customer. In four cases Microsoft was compelled to provide responsive information regarding five accounts to law enforcement. One case is still outstanding and pending a resolution.”
As can be seen from the numbers above, the vast majority of law enforcement requests and disclosures do not relate to enterprise customers – they are related to consumer services (e.g. Hotmail, Xbox, consumer Skype services) as opposed to Azure, Office 365, CRM Online etc:
“What is the difference between a consumer and an enterprise customer?
A consumer service is generally one subscribed to and used by an individual in his or her personal capacity. Some examples include Hotmail/Outlook.com, OneDrive (which was previously called SkyDrive), Xbox Live and Skype. For purposes of this report, “enterprise customer” generally includes those organizations or entities (commercial, government or educational) that purchase more than 50 “seats” for one of our commercial cloud offerings, such as Office 365, Azure and Exchange Online and CRM Online.”
Summary
In procuring any service, whether technology-related or not, it is sensible to conduct due diligence.
The unfortunate common practice of cloud washing means this due diligence is a little more difficult to undertake; however with the myths dispelled in this blog, hopefully making those choices will be more informed and a little easier. Microsoft has also published a list of 10 questions: Top questions you should ask a cloud service provider when you are considering the cloud for your IT services which may help you assess the options and conduct due diligence on all options.
As always, if your business is going through any changes and you’re exploring your cloud options, don’t hesitate to get in touch at [email protected].

Leave a Reply